— Proton Exploit
Por um escritor misterioso
Last updated 14 maio 2024

WannaCry - Important lessons from the first NSA-powered ransomware cyberattack

Proton Pass Retains Passwords in Memory

Instruments, Free Full-Text

Development of a Typical Distribution Function of Relaxation Times Model for Polymer Electrolyte Membrane Fuel Cells and Quantifying the Resistance to Proton Conduction within the Catalyst Layer
Will on X: 🔎 Somewhat interesting software pirating site enesoftware[.]com that targets other cybercriminals too, offering builders & panels for sought after #malware like MarsStealer, Anubis, and Alien Actor: uhogiwubi5 (enesoftware[.]com/writer
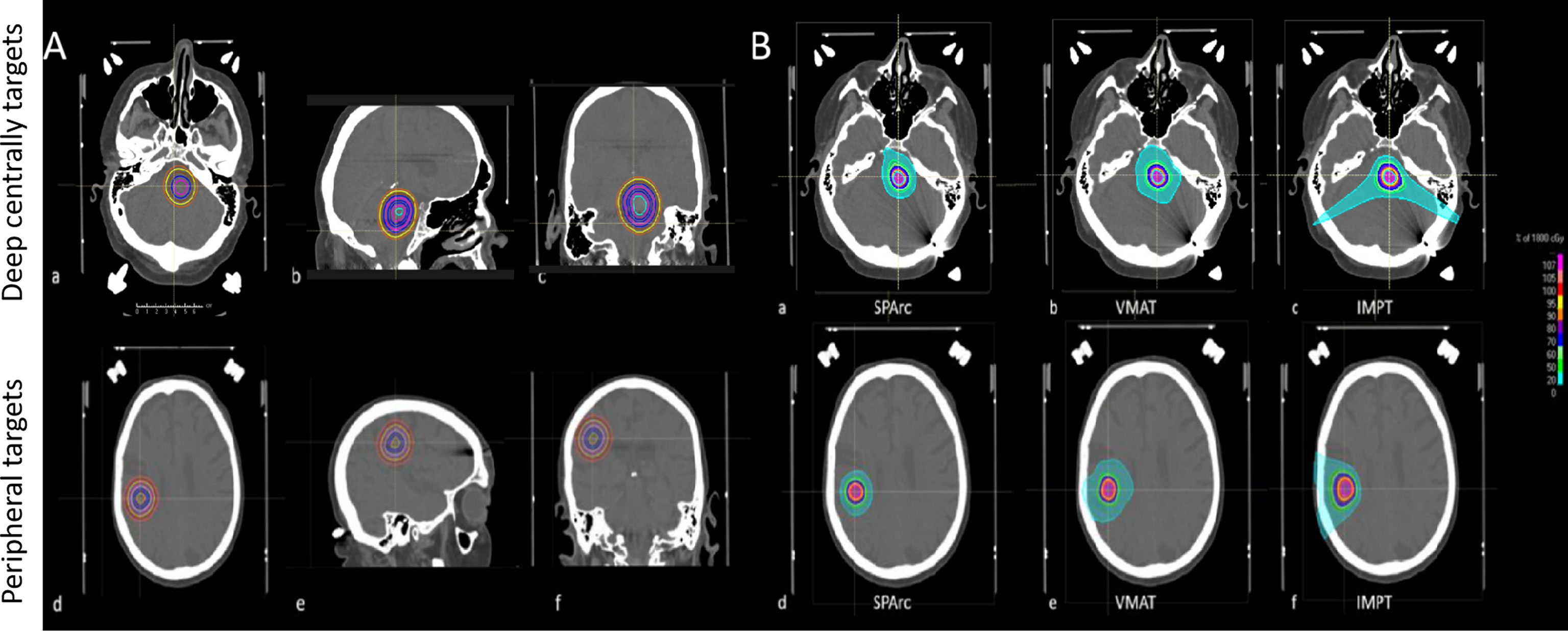
Frontiers Redefine the Role of Spot-Scanning Proton Beam Therapy for the Single Brain Metastasis Stereotactic Radiosurgery

Defending online freedom with technology
Proton transfer kinetics of transition metal hydride complexes and implications for fuel-forming reactions - Chemical Society Reviews (RSC Publishing)

An Emerging Chemistry Revives Proton Batteries - Guo - Small Methods - Wiley Online Library

All ProtonVPN apps are 100% open source - ProtonVPN Blog
Blaster — THM. Throughout this room, we'll be looking…, by Fallen sky
Recomendado para você
-
wearedevs.net Competitors - Top Sites Like wearedevs.net14 maio 2024
-
 Wearedevs14 maio 2024
Wearedevs14 maio 2024 -
 anyone noticed how Comet unbit the dust? : r/ROBLOXExploiting14 maio 2024
anyone noticed how Comet unbit the dust? : r/ROBLOXExploiting14 maio 2024 -
 🔥 NEW FREE ROBLOX EXPLOIT 🔥 ELECTRON ✓ Free LVL7! ✓14 maio 2024
🔥 NEW FREE ROBLOX EXPLOIT 🔥 ELECTRON ✓ Free LVL7! ✓14 maio 2024 -
 WeAreDevs World Congress 22 on the App Store14 maio 2024
WeAreDevs World Congress 22 on the App Store14 maio 2024 -
get-exploit/getexploit.lua at main · astriaInight/get-exploit · GitHub14 maio 2024
-
Is SmileDirectClub reliable and safe? - Quora14 maio 2024
-
 Krystal Eight (@KrystalEight) / X14 maio 2024
Krystal Eight (@KrystalEight) / X14 maio 2024 -
Mohsen Esmailpour on LinkedIn: #developer #developerlife #github #chatgpt #stackoverflow #14 maio 2024
-
![Roblox New Keyless Executor/Exploit ELECTRON [Level 9 & Bypass] 2023](https://i.ytimg.com/vi/7BUrPkEP9dc/sddefault.jpg) Roblox New Keyless Executor/Exploit ELECTRON [Level 9 & Bypass] 202314 maio 2024
Roblox New Keyless Executor/Exploit ELECTRON [Level 9 & Bypass] 202314 maio 2024
você pode gostar
-
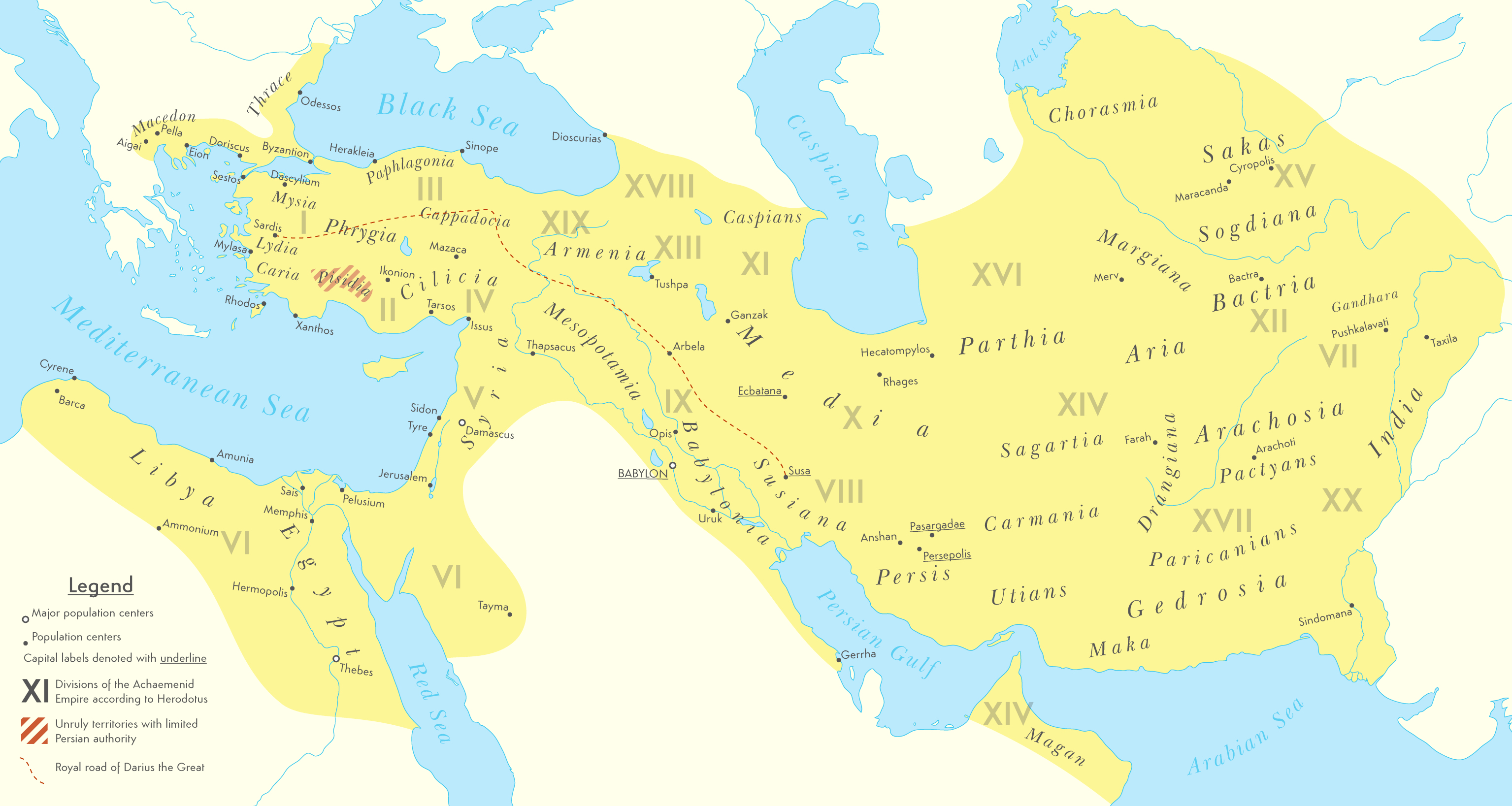 Achaemenid Empire - Wikipedia14 maio 2024
Achaemenid Empire - Wikipedia14 maio 2024 -
 We Found JUMBO JOSH in Minecraft! (Garten of BanBan)14 maio 2024
We Found JUMBO JOSH in Minecraft! (Garten of BanBan)14 maio 2024 -
 Alphabet Lore But It`s Reverse (Z-A) by ALPHABETTER14 maio 2024
Alphabet Lore But It`s Reverse (Z-A) by ALPHABETTER14 maio 2024 -
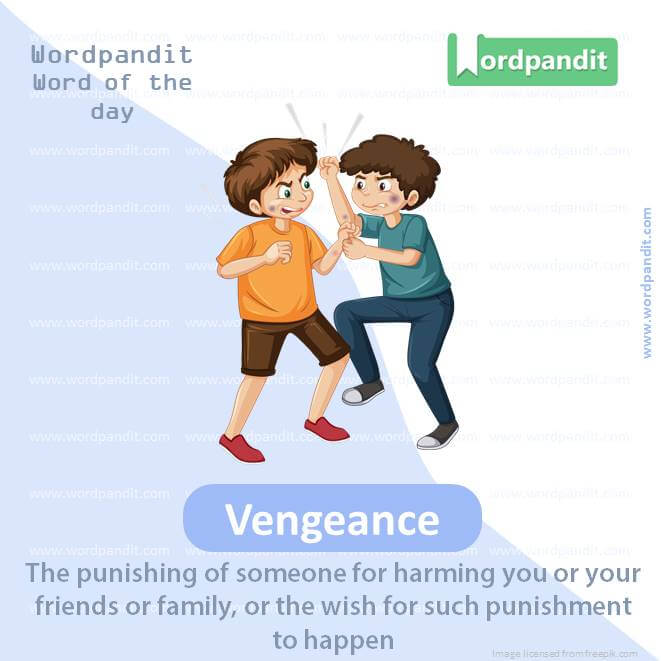 Daily Vocabulary from 'The Hindu': July 16, 202314 maio 2024
Daily Vocabulary from 'The Hindu': July 16, 202314 maio 2024 -
/i.s3.glbimg.com/v1/AUTH_bc8228b6673f488aa253bbcb03c80ec5/internal_photos/bs/2021/7/D/ybAydRSfySMPa9TYUNFg/luisa.png) Luisa Stefani se torna 6ª tenista do Brasil na história a atingir o top 10, tênis14 maio 2024
Luisa Stefani se torna 6ª tenista do Brasil na história a atingir o top 10, tênis14 maio 2024 -
 Pros and Cons of Using a VPN for Gaming - CNET14 maio 2024
Pros and Cons of Using a VPN for Gaming - CNET14 maio 2024 -
 CapCut_together again download apk14 maio 2024
CapCut_together again download apk14 maio 2024 -
 Draw Anime & Manga for Android - Download14 maio 2024
Draw Anime & Manga for Android - Download14 maio 2024 -
 Tapu Koko V, Pokémon14 maio 2024
Tapu Koko V, Pokémon14 maio 2024 -
 Family Tree - Anime Characters Database Wiki14 maio 2024
Family Tree - Anime Characters Database Wiki14 maio 2024
